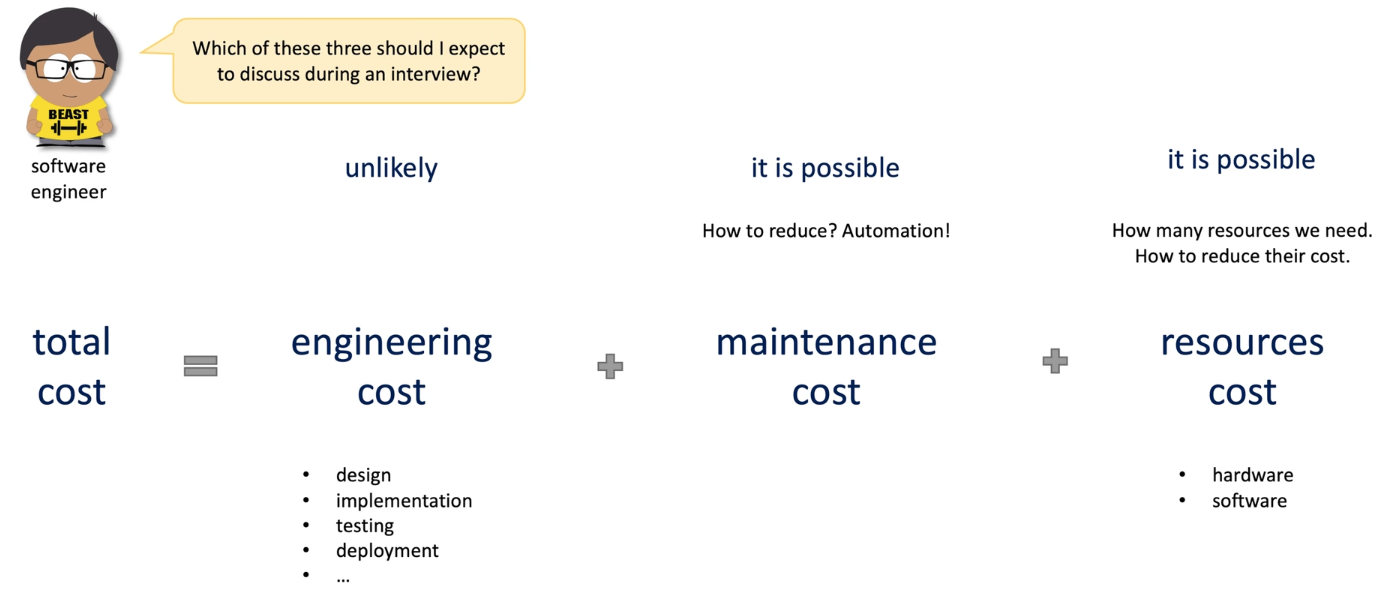
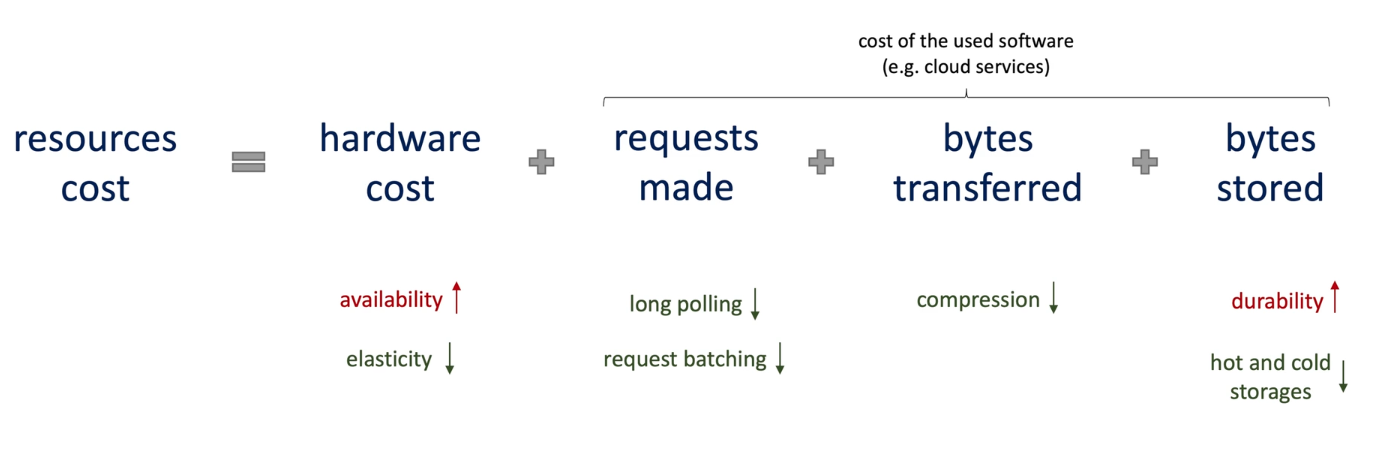
2.9 Maintainability, Security, Cost
Maintainability
failure modes and mitigations
- if some component fails, what happens to the rest of the system?
- how the system handles network partitions?
- how we want the system to handle network partitions
monitoring
- how do we monitor the health of the system?
- in case of a system failure,how do we know what exactly is broken?
testing
- how to test each individual component?
- how to test dat flows end-to-end?
deployment
- how to deploy regular changes safely?
- how to roll back bad changes quickly?
Security
CIA triad
- Confidentiality
- Integrity
- Availability
Identity and permissions management
- who can access the system?
- who can access what in the system?
- how to implement authentication and authorization in the system?
Infrastructure protection
- is the system protected from DDoS attacks
- is it protected from other common attacks, such as SQL injection or cross-site scripting?
- should we use a web application firewall or an API gateway to implement protection?
Data protection
- how to protect data at rest?
- how to protect data in transit?